Cyber News
Pitt Tech Offers Smart Choices For Tech, Crypto, and Cybersecurity
Making Technology Easier for Anybody
If you can’t find what you are looking for, feel free to contact me directly for more suggestions or solutions at Pitttechnologysolutions@gmail.com

Products & Services
Below are some amazing products and services
Each product will have a small review or information box to better assist you with your choice. Scroll down for more info.

The Meta Quest 3 128GB
The Ray-Ban – Meta Smart Glasses – Wayfarer – Shiny Black/Clear are a pair of smart glasses that are designed to look like regular Ray-Ban Wayfarer sunglasses. They have a number of features that make them smart, including:
- A built-in camera that can take photos and videos
- Speakers and microphones for listening to music and making calls
- Touch controls on the right arm of the glasses
- A voice assistant that can be used to control the glasses and other smart devices

The Meta Quest 3 128GB
The Meta Quest 3 128GB is a game-changer for tech enthusiasts like us. Its powerful performance makes it an excellent tool for cybersecurity exploration, and the mixed reality experience adds a unique dimension to cryptocurrency research. However, always exercise caution when using VR and AR applications, and ensure your security remains a top priority. The inclusion of the Asgard’s Wrath 2 Bundle sweetens the deal, offering both professional and recreational value.

MSI 2023 Cyborg 15.6″ 144HZ FHD Gaming Laptop, 13th Gen Intel Core i7-13620H, NVIDIA GeForce RTX 4050, 32GB DDR5 RAM, 1TB NVMe SSD, Wi-Fi6, Backlit Keyboard, Win11
As a cybersecurity expert, I had the opportunity to review the MSI 2023 Cyborg gaming laptop, and I must say, it impressed me on multiple fronts. This laptop combines cutting-edge hardware with sleek design and enhanced security features. The laptop comes with Windows 11, which offers enhanced security features like Secure Boot, Windows Hello facial recognition, and improved system protections. Equipped with the 13th Gen Intel Core i7-13620H processor and NVIDIA GeForce RTX 4050 graphics card, the Cyborg laptop delivers exceptional performance. Whether you’re gaming, rendering videos, or multitasking, it handles everything with ease.

USB Wall Charger Surge Protector 5 Outlet Extender with 4 USB Charging Ports
The USB Wall Charger Surge Protector 5 Outlet Extender with 4 USB Charging Ports and 1 USB-C Outlet is a well-designed and feature-rich solution for addressing the power and charging needs of modern electronics. Its 1800J surge protection, along with the multi-layer safety mechanisms, ensures device safety while catering to the simultaneous charging of multiple devices. The 3-sided design and spacing between outlets are practical enhancements that make it a user-friendly choice.

Cybersecurity For Dummies (For Dummies (Computer/Tech)) 2nd Edition
This book is an accessible and practical guide that provides a comprehensive introduction to cybersecurity. It breaks down complex concepts, offers real-world examples, and equips readers with the knowledge needed to enhance their digital security. While some specific technologies mentioned may become outdated, the foundational principles remain relevant, making it a valuable resource for beginners and non-technical readers.
JEPWCO G4 Pro Anti Spy Detector for Wireless Device: Home, Office, or Travel

The JEPWCO G4 Pro Anti Spy Detector is a portable device that claims to detect wireless audio bugs and cameras. This signal detector can detect eavesdropping devices, wired and wireless cameras, GPS locators and etc. This device is perfect for detecting unfamiliar enviornments such as vehicles, hotels, and AirBnB stays.
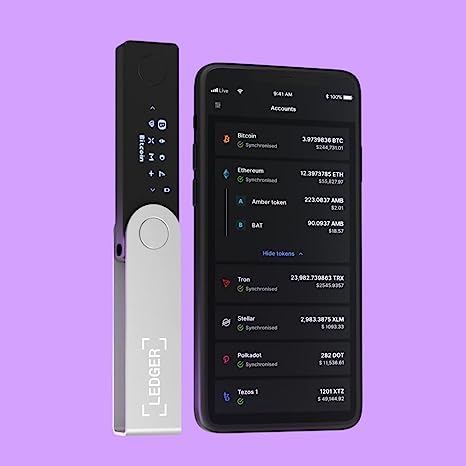
Ledger Nano X
The Ledger Nano X is a highly secure hardware wallet with robust security features, user-friendly design, and strong performance. It employs a Secure Element chip, secure OS, and PIN code system to protect against cyber threats and unauthorized access. The Nano X offers protection against malware, phishing attacks, physical tampering, and uses a recovery phrase for key restoration. With a 2.4-inch color screen and Bluetooth connectivity, it provides an intuitive interface, supports multiple cryptocurrencies, and integrates with Ledger Live software. The Nano X ensures reliable and fast transaction signing for smooth cryptocurrency transfers, contributing to a seamless user experience.

HUANUO Dual Monitor Stand, Adjustable Spring Monitor Desk Mount for 13-27 inch, Holds Max 14.3lbs, Computer Monitor Arms with Wide Range of Motion for Home Office
The HUANUO Dual Monitor Stand has become an indispensable addition to my home office. Its flexibility, durability, and ergonomic benefits have enhanced my productivity and overall well-being. If you’re seeking an ergonomic and space-saving solution for your dual monitors, I highly recommend the HUANUO monitor stand. Elevate your home office experience with this exceptional desk mount!

Smart Home Security
Investing in home security and smart devices is crucial in today’s digital era, offering enhanced security, convenience, and efficiency. These devices provide advanced protection through surveillance cameras, smart locks, and sensors, allowing real-time monitoring and alerts. Remote management and automation ensure the safety of loved ones and property, even when homeowners are away. Smart thermostats, lighting systems, and appliances enable remote control, energy optimization, and personalized experiences. Centralized control through a single app or voice command streamlines home management. Smart devices improve energy efficiency, reduce utility bills, and contribute to sustainability. They also offer future-proofing with updates and new features. Some insurance providers offer benefits and cost savings for homeowners with installed home security systems.

TOTU 11-in-1 Adapter with Ethernet, Compatible for Mac Pro and Other Type C Laptops
The TOTU 11-in-1 Adapter with Ethernet provides convenient connectivity options. However, it’s essential to consider potential security vulnerabilities associated with introducing additional ports. Ensure you purchase from a reputable brand, keep firmware/software updated, encrypt sensitive data, and exercise caution when connecting to networks. Taking these precautions will help mitigate potential risks while enjoying the adapter’s benefits.

Norton 360 Software
Norton 360 Premium delivers exceptional cybersecurity protection with a seamless user experience. It combines antivirus, VPN, and a password manager into one comprehensive package. Not only does it effectively safeguard against online threats, but it also prioritizes privacy. The VPN ensures anonymous browsing, while the password manager simplifies secure logins. For peace of mind and a user-friendly solution, Norton 360 Premium is an excellent choice.

Frequently Asked Questions
01.
What is cybersecurity?
Cybersecurity is the practice of protecting networks, systems, and programs from digital attacks. These attacks are usually aimed at accessing, changing, or destroying sensitive information, extorting money from users, or interrupting normal business processes.
02.
What are the most common types of cybersecurity threats?
The most common types of cybersecurity threats include malware, phishing, ransomware, denial-of-service attacks, and data breaches. Malware is malicious software that can damage systems or steal data. Phishing is a type of social engineering attack in which attackers try to obtain sensitive information by pretending to be a legitimate entity. Ransomware is a type of malware that encrypts data and demands payment in exchange for unlocking it. Denial-of-service attacks are attempts to make a system or network unavailable by flooding it with requests. Data breaches occur when unauthorized users gain access to an organization’s confidential data.
03.
What can I do to protect my personal information online?
To protect your personal information online, you should take the following steps:
• Use strong, unique passwords for all online accounts.
• Enable two-factor authentication.
• Be aware of phishing scams and never click on links in emails or messages from unknown senders.
• Use a virtual private network (VPN) when connecting to public Wi-Fi networks.
• Use an ad-blocker to reduce the risk of malicious ads.
• Be careful when downloading software, only downloading it from trusted sources.
• Monitor your online accounts for any suspicious activity.
04.
How can I protect my organization from cybersecurity threats?
Organizations and individuals can protect themselves from cybersecurity threats by implementing a comprehensive security strategy that includes the following measures:
• Implementing strong access control policies and procedures.
• Regularly patching systems and software.
• Training employees on cybersecurity best practices.
• Installing anti-virus and anti-malware software.
• Regularly backing up data.
• Implementing multi-factor authentication.
• Monitoring network activity for suspicious activity.

